- described in RFC 7296 (initially RFC 5996)
- offers dynamic key exchange and peer authentication
- addresses measures to fix vulnerabilities of IKEv1 (anti-DoS)
- supports Extensible Authentication Protocol (EAP)
- it is not backward compatible with IKEv1
- operates in two phases
- industry standard, can operate in multivendor environment
- Phase 2 is CHILD_SA, first message pair is IKE_AUTH, additional CHILD_SA can be sent for rekey and information messages (data policy)
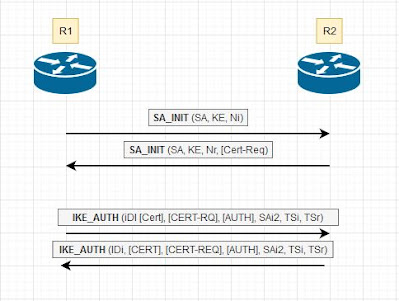
R1 is the Initiator / R2 is the Responder
SA – security association
KE – Key exchange
Nr,Ni – Nonce
Cert-Req – Certificate Request
Cert – Certificate
IDi – Identification (Initiator/Responder)
TSi – Traffic selector – Initiator
TSr – traffic selector – Responder
IKEv2 authentication methods:
- pre-shared keys (PSK)
- digital signatures
- EAP
IPSec
IPSec consist of two main security protocols:
- Authentication Header (AH- IP protocol ID 51) – used for authentication and Integrity, enforces anti replay protection (receiving host sets replay bit in the header). AH is applied to datagram only.
- Encapsulation Security Payload (ESP- IP protocol ID 50) – used to provide confidentiality (encryption), data origin authentication, integrity, optional anti-replay service. Performs encryption at the IP packet layer, support symmetric algorithms by default 56-bit DES.
The AH can be applied alone or together with the ESP.
IPSec supports following standards:
- Data encryption standard (DES), Triple DES (3 DES)
- Delffie – Hellman (D-H)
- Message Digest 5 (MD5)
- Rivest, Shamir, and Adelman (RSA) signatures
- IKEv1/v2
- Certificate Authorities
IPSec operates in two modes:
- Tunnel mode – A new IP header is created in place of the original this allow for encryption of entire original packet. Tunnel mode is used to encrypt traffic between secure IPSec Gateways i.e. Site to Site VPN or Cisco VPN Client and a IPSec Gateway.
- Transport mode – The AH or ESP is inserted behind the IP header, the IP header can be authenticated but not encrypted. Use example would be an encrypted Telnet or Remote Desktop session from a workstation to a server.
In transport mode IP header is exposed.
Smart Defaults – this feature minimize FlexVPN configuration process. For example is following configuration steps can be skipped:
- IKEv2 Proposal
- IKEv2 Policy
- IPSec transform-set
- IPSec profile
default values will be picked, to verify default values:
- sh crypto ikev2 proposal
- sh crypto ikev2 policy
- sh crypto ipsec transform
- sh crypto ipsec profile
The think to remember is to use “default” as a name for the ikev2 profile.
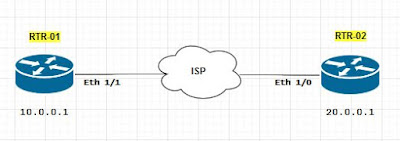
LAB. Site to site FlexVPN with SVTI (using smart defaults)
RTR-01
crypto ikev2 keyring FlexVPN
peer rtr-02
address 20.0.0.1
pre-shared-key local cisco
pre-shared-key remote cisco
crypto ikev2 profile default
description --->Basic FlexVPN<---
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local FlexVPN
crypto ikev2 dpd 10 3 on-demand
interface Tunnel200
description FlexVPN-to-rtr-02
ip address 10.120.0.1 255.255.255.252
tunnel source Ethernet1/1
tunnel mode ipsec ipv4
tunnel destination 20.0.0.1
tunnel protection ipsec profile default
RTR-02
crypto ikev2 keyring FlexVPN
peer rtr-01
address 10.0.0.1
pre-shared-key local cisco
pre-shared-key remote cisco
crypto ikev2 profile default
description --->Basic FlexVPN<---
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local FlexVPN
crypto ikev2 dpd 10 3 on-demand
interface Tunnel200
description FlexVPN-to-rtr-01
ip address 10.120.0.2 255.255.255.252
tunnel source Ethernet1/0
tunnel mode ipsec ipv4
tunnel destination 10.0.0.1
tunnel protection ipsec profile default
Verification:
RTR-01-HUB#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
1 10.0.0.1/500 20.0.0.1/500 none/none READY
Encr: AES-CBC, keysize: 256, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/248 sec
CE id: 1001, Session-id: 1
Status Description: Negotiation done
Local spi: 6445B887B3DC849B Remote spi: CB227544A6FD4612
Local id: 10.0.0.1
Remote id: 20.0.0.1
Local req msg id: 2 Remote req msg id: 0
Local next msg id: 2 Remote next msg id: 0
Local req queued: 2 Remote req queued: 0
Local window: 5 Remote window: 5
DPD configured for 10 seconds, retry 3
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : Yes
IPv6 Crypto IKEv2 SA
RTR-01-HUB
RTR-02#show crypto ikev2 sa detailed
IPv4 Crypto IKEv2 SA
Tunnel-id Local Remote fvrf/ivrf Status
2 20.0.0.1/500 10.0.0.1/500 none/none READY
Encr: AES-CBC, keysize: 256, Hash: SHA512, DH Grp:5, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/159 sec
CE id: 1001, Session-id: 1
Status Description: Negotiation done
Local spi: CB227544A6FD4612 Remote spi: 6445B887B3DC849B
Local id: 20.0.0.1
Remote id: 10.0.0.1
Local req msg id: 0 Remote req msg id: 2
Local next msg id: 0 Remote next msg id: 2
Local req queued: 0 Remote req queued: 2
Local window: 5 Remote window: 5
DPD configured for 10 seconds, retry 3
NAT-T is not detected
Cisco Trust Security SGT is disabled
Initiator of SA : No
IPv6 Crypto IKEv2 SA
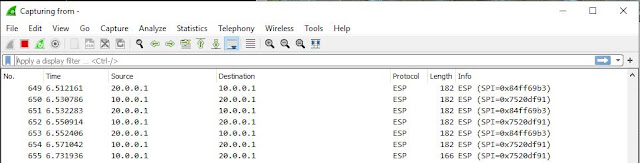
Wireshark capture of the test ping from rtr-01 to rtr-02.